VpnMentor’s cybersecurity research team led by Noam Rotem and Ran Locar has revealed unprotected AWS S3 container with over 5.5 million files and over 343GB in size it is not required.
Discovery timeline and owner reaction
Sometimes the extent of data breaches and the owner of the data are obvious, and the problem was resolved quickly. But these times are rare. Most of the time, we need days of investigation before we understand what is at stake or who is disclosing the information.
Understanding the violation and its potential impact takes careful attention and time. We work hard to publish accurate and reliable reports, making sure everyone who reads them understands their seriousness.
Some parties dispute the facts, ignore our research, or diminish its impact. So we need to be thorough and make sure everything we find is right and true.
In this case, after a few days of research, we recognized the possibility that the information belongs to InMotionNow and contacted the company later with our discovery. Although the unprotected S3 bucket is now closed, none of the company ever responded to attempts to gain access, so we cannot confirm ownership.
- Discovery date: December 20, 2019
- Date InMotionNow (alleged owner of the data) reported: December 26, 2019
- Date Amazon announced: 29 December 2019, 7 January 2020 and 30 January 2020
- Date bucket closed: February 17, 2020
- Date of notification of other companies: March 16, 2020
Company profiles
In this particular case, our research team was unable to verify without a shadow of a doubt who exactly owns the disclosed information. For this reason, we have decided that it is very important to let the general public know whose information and which information is vulnerable to the lack of standard cybersecurity procedures.
Our research led us to it InMotionNow owns the data. We addressed them, and no one answered, and the bare bucket had no clear indication that it was theirs. With that in mind, we are including all companies whose information was found in the bucket. If it actually belongs to InMotionNow, they know who is disclosing the information, and if not, companies can investigate for themselves. Our team has also reached these companies on March 16, 2020.
Founded in 1999, InMotionNow is a project management software company headquartered near Raleigh, North Carolina. They have FDA-compliant safety standards aimed at the verticals of their target customers.
Here is a non-exhaustive list of companies whose marketing material was found in an unprotected S3 bucket:
Cyber security company ISC2.org several pieces of information were also included in this violation.
Brotherhood Mutual Insurance Company, which primarily serves religious institutions throughout the United States.
Universities such as the state of Kent in Ohio and Purdue in Indiana, The S3 group also contained numerous files and data.
Potawatomi Hotel & Casino in Milwaukee, Wisconsin.
Consumer Electronics Company, Zagg (ZAGG), which designs and produces mobile accessories.
A non-profit organization, the Freedom Forum Institute, which supports the United States ’First Amendment freedoms for all.
Organizations were found to be affected by different health care regulations. They include, but are not limited to:
Myriad genetics (MYGN) – Genetic and disease testing company.
Performance health – Provider of physiotherapy equipment and supplies.
Examples of records
Here is a list of information that our research team found and was able to identify:
The data is affected
- Analytics reports
- Internal presentations, including:
- Company strategy
- Annual revenue figures
- Number of existing customers
- Training materials
- Internal customer requests, including:
- Name of the applicant
- Project name and details
- Marketing strategies and collateral
- Product labels
- Business intelligence
- Mailing lists with relevant personal information
Lists of university donors, including:
- Full names
- Personal and work messages
- Direct telephone numbers
- Credentials (degree, school, year)
- Amount donated
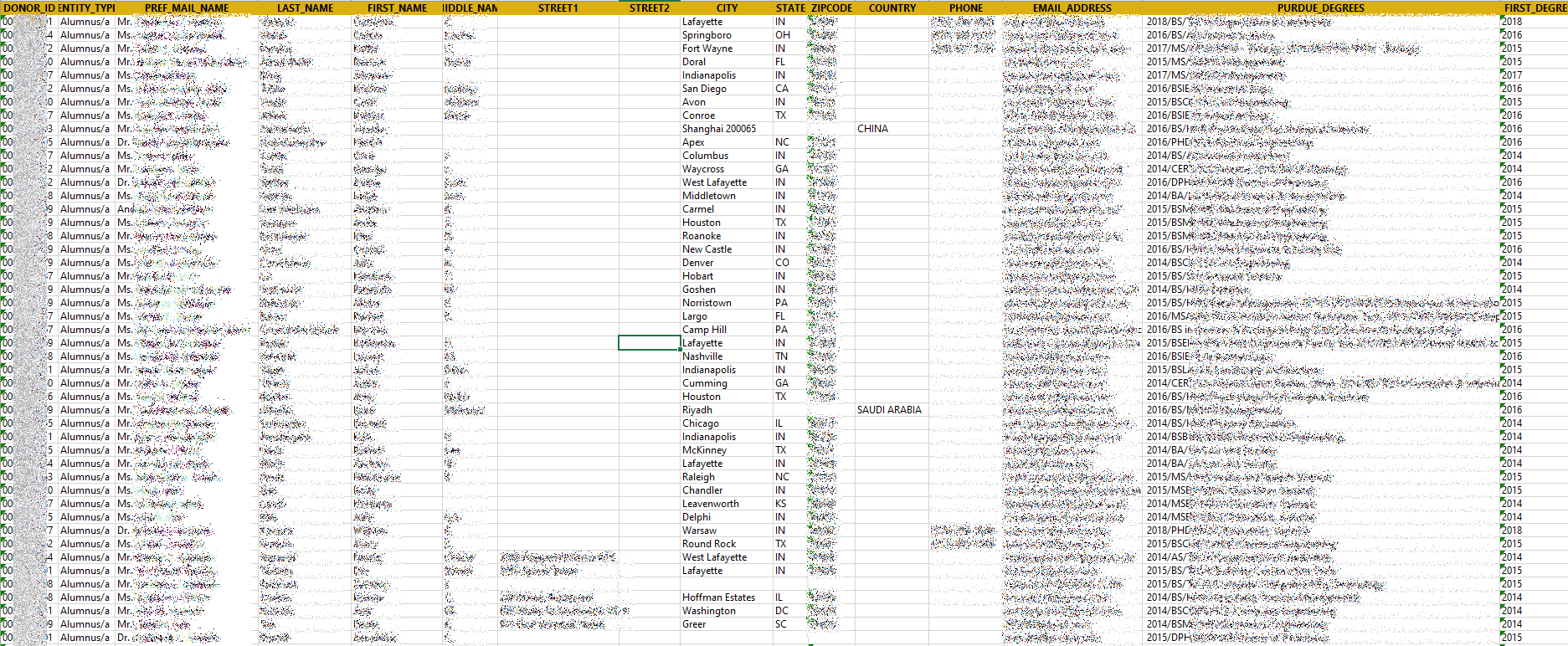
List of university donors
Countries affected
These are the countries where we found customers who were included in the data breach, but we didn’t open every file, and it’s possible that there are more customers in other countries affected.
- France
- United States
Impact of data breaches
Confidential information
Products covered by this data breach often contain private and / or confidential information. Promises of secure facilities and systems are key to customers, such as the military and its supply chain – and breaking this guarantee is not only a failure of services, but also a potential security risk.
Identity theft
Knowing an individual’s full name, birthday, and yes, even a prison record can give criminals enough information to steal a person’s identity.
Identity theft does not always mean that a thief claims to be a certain person in real life; it also gives them a chance engage in credit fraud, clear your bank account and cheat against the family, friends and other persons of the victim of identity theft.
Copyright Infringements
Anyone with access to the myriad of copyrighted documents contained in this S3 bucket could easily download them free of charge for their content and also download them illegally torrent network that is available to everyone for free.
Fraud
The combination of brand materials and contact information makes it a thumb for anyone with harmful motives for fraud. It is possible give false testimony from universities and mark insider information to gain false credibility.
Corporate espionage
Size unencrypted logins by administrators appear to be available for this violation. Loss of control of this access may result in cybercriminals taking over accounts and obtaining otherwise confidential information about stores, employees, and customers.
Expert advice
The company that owns this bucket could easily have avoided this data breach if it had taken some basic security measures to protect the S3 bucket. These include:
- Protect your servers.
- Implement the appropriate access rules.
- Never leave a system that does not require authentication open on the Internet.
Every company can repeat the same steps regardless of size. For more information on protecting your business, visit our website a guide to protecting your website and online database from hackers.
Open the S3 bucket attachment
It’s important to note that open, publicly viewable S3 buckets are not an AWS bug. They are usually the result of an error on the part of the bucket owner. Amazon provides detailed instructions for AWS users so they can protect their S3 buckets and keep them private.
For this unprotected S3 bucket, the quickest way to fix the error is:
- Make the group private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to the S3 bucket to further limit who can use it from each entry point.
For those affected by the data breach
If you suspect that you may have personal or business information about this unprotected S3 bucket – and are concerned about how this breach may affect you or other data breaches in general, read on. the complete guide to online privacy so that you can better protect your online future. It shows you how cybercriminals target Internet users, and the steps you can take to stay safe.
You can also hide part of the collected data using VPN the owner of this bucket. The VPN covers your IP address and country of residence, giving you an extra level of protection even if your information is revealed.
How and why we discovered the violation
The VpnMentor research team found a misdefined bucket as part of a a huge web mapping project. Our researchers use port scanning to examine specific IP blocks and test open holes in systems for vulnerabilities. They examine each hole for data leaks.
When they find a data breach, they use expert techniques to verify the identity of the owner of the S3 bucket. We will then notify the company of the violation. If possible, we will also notify those affected by the violation.
We were able to use the S3 bucket because it was completely unprotected and unencrypted. Using a web browser, the team had access to all the files in the bucket.
The purpose of this web mapping project is to make the Internet safer for all users. As ethical hackers, we have a duty to notify a company when we detect deficiencies in their network security.
However, These ethics also mean that we also have a responsibility to the public. This is especially true when a company’s data breach contains such a large amount of private and sensitive information.
About us and previous reports
vpnMentor is the world’s largest VPN verification site. The Research Lab is a pro bono service that aims to help the online community defend against cyber threats and train organizations on how to protect user data.
In the past, we have detected a violation in LightInTheBox that compromised the information of its customers. We also recently revealed that a company owned by the largest hotel chain, AccorHotels, revealed more than 1 TB of guest information. You can also read our VPN leakage report and our privacy statistics report.

